A Document Management Solution using Blockchain
Abstract
Computer systems are relatively simple to secure when used by a small group of people. Things begin to get complicated when we want to allow multiple people across multiple organizations and geographic locations to interact with the system. VPN partially solves this problem by keeping the solution in-network. However, VPN still leaves your internal network exposed to anyone with access. It also requires you to manage certificates and track who has them. In addition, the on-boarding process is complex especially when working with multiple parties spread around the globe. In this paper I will use an Enterprise Document Management System (eDMS) to demonstrate how blockchain can solve all these problems, allowing a truly global computer system accessible by stake holders around the world with a trivial on-boarding process. As an added benefit this system will provide inherent audit-ability and fraud detection.
Introduction
Blockchain platforms like Ethereum allow one to create smart contracts. Smart contracts are “applications that run exactly as programmed without any possibility of downtime, censorship, fraud or third-party interference.” Multiple smart contracts can be linked together, in a similar way to modules and dependencies in traditional programming languages. This allows one to create a highly configurable and modularized set of contracts (i.e. business rules) that can be used to “command and control” a traditional content management system. For a more detailed overview see my previous article that explains why blockchain changes everything.
Document Management
What differentiates an enterprise DMS from a simple document storage service like Dropbox is the complex layer of rules and permissions that dictate how a document can be interacted with. At its core an enterprise DMS is a set of business rules that sit on top of a simple document storage service, acting as a command and control of said service.
In a traditional DMS the business logic lives inside of the primary storage application. In the blockchain model these two pieces are split up into:
- The Simple Document Management Interface through which users interact with the documents. This consists of the UI and a document storage medium (e.g. S3 or Box).
- Smart contracts containing business logic rules related to roles, permissions and workflows.
Viewing Documents
When a user, Alice, previews a document, the Simple Document Management Interface will verify with the blockchain that the document loaded into her browser is indeed the document she intended to view. If a malicious user, Eve, managed to compromise the storage medium and change some values on the stored document, the hash of the document being viewed by Alice will not match the hash stored in the blockchain. Alice will see a big red warning sign that the document she is viewing is in an altered state. (Note: the blockchain does NOT store the
valid document, it only stores the signature of the valid document. It will still be up to the storage medium to keep copies of older document version. In the event of a breach, a protocol will be in place to backtrack the document versions in the storage medium until a document with a hash matching the hash in the blockchain is found.)
Document Workflows
When Alice attempts to perform an activity, the Simple Document Management Interface will verify with the blockchain that the attempted activity is allowed. If it is allowed, the new state of the document along with its new hash and the user who performed the action will be recorded in the blockchain. If the activity is not allowed the Simple Document Management Interface can reflect that to the user (e.g. error messages, disabled elements, hiding fields, etc.). All performed activity will be forever saved in the blockchain and can never be modified.
If a user attempts to circumvent the Simple Document Management Interface they will quickly become discouraged by the overwhelming and unyielding power of Math. No state changes can be applied to a Document Smart Contract without conforming to the immutable rules implemented by the contract creator. In the event that a malicious user circumvents the blockchain verification and saves a modified document to the storage medium, it will become immediately apparent to anyone viewing the document when the document hash does not match the hash saved in the blockchain. (As stated above, this can be easily rectified by backtracking the document versions in storage until a matching document is found.)
Smart Contracts
A prototype DMS can be implemented with just 3 smart contracts.
1. A Role smart contract that describes a user role and the permissions granted to that role.
2. A Workflow smart contract that defines workflow steps and a list of Role smart contracts that can interact with the workflow.
3. A Document smart contract that represents a document.
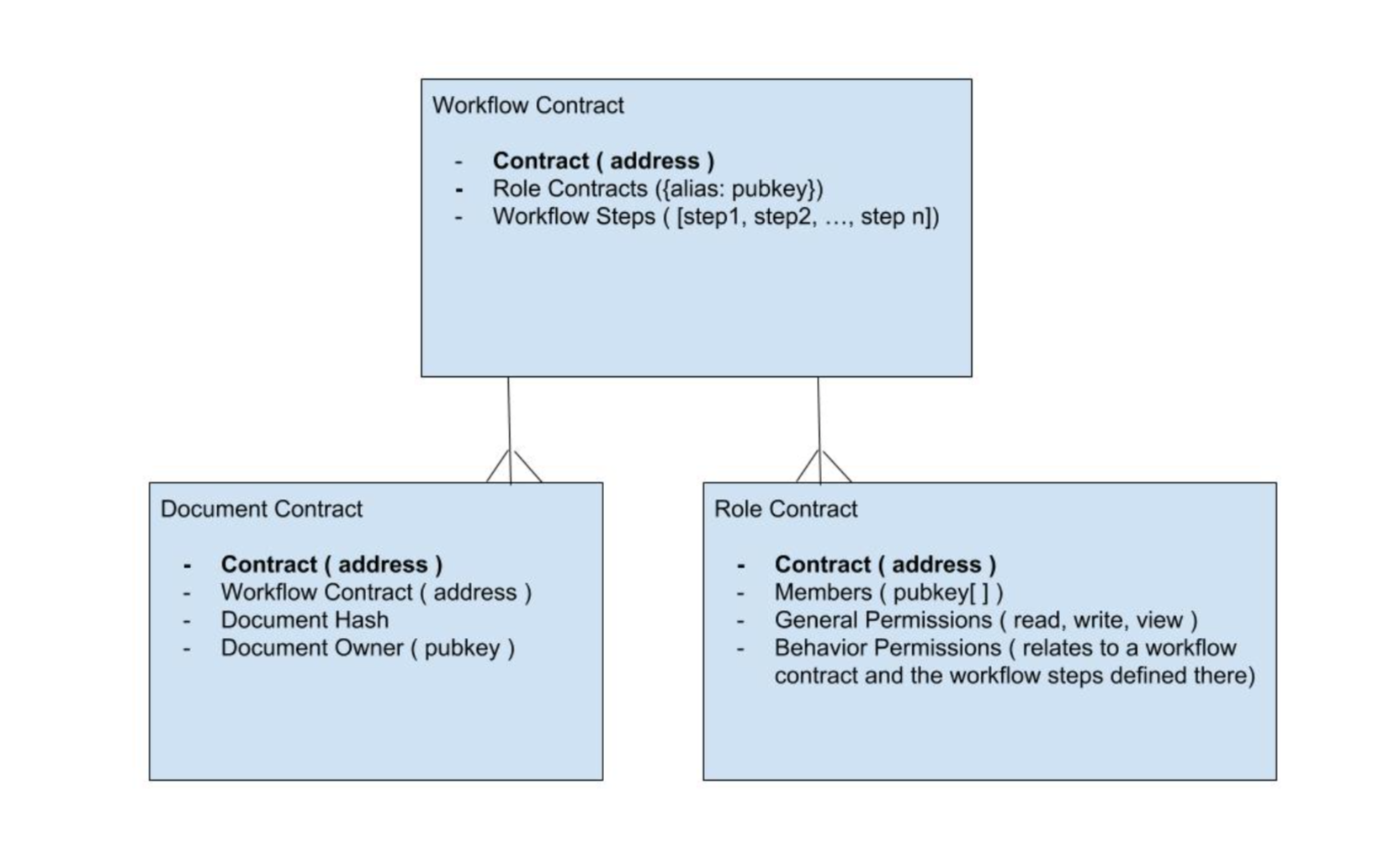
Each of these smart contracts can be thought of as classes that can be instantiated as needed. When a particular smart contract instance is needed, it is compiled and persisted to the blockchain. For our prototype we would instantiate 3 Role contracts (viewer, author, approver) and 1 Workflow contract with 3 workflow steps (draft, pending approval, effective). Users will use the MetaMask Chrome browser extension to generate their public keys. The admin can add and remove users from the different role contracts.